Home Industry Banking and finance Role-Based Access Control (RBA...
Banking And Finance
.webp)
CIO Bulletin
15 March, 2023
By Prashanthi Gutha
Organizations today juggle hundreds of cloud apps, remote teams, and ever-tightening compliance demands. Beneath polished dashboards and seamless single sign-on lies a patchwork of access rules, ad-hoc permissions, and manual processes. Each represents a potential weak point.
From years of designing secure systems in high-stakes environments, one pattern stands out: piecemeal access control collapses at scale. Permissions drift. Audits turn into reconciliation marathons. Incidents often arise from outdated or excessive access rights.
The issue isn’t a lack of tools, but the absence of a scalable, cohesive framework. Role-Based Access Control (RBAC) provides that structure, replacing tangled individual permissions with clear, role-aligned boundaries.
Okta’s mature identity platform brings RBAC to life for complex enterprises. With disciplined implementation, it becomes more than a safeguard. It’s a growth enabler that ensures the right people have the right access at the right time.
In Okta, roles are bundles of permissions that define what an account can do within specific scopes, such as an application, dataset, or API. RBAC assigns these roles so access aligns with job functions, eliminating the need to grant each permission manually. This reduces errors and saves administrative time.
Okta Workflows uses a delegation model: the Super Administrator oversees everything, delegates to Workflows Administrators, and they assign specialized roles like Workflows Auditor or Connection Manager. This layered approach limits permissions, reduces risk, and preserves separation of duties.
When roles directly match real-world job functions, administration becomes simpler, and compliance structures are built in from day one.
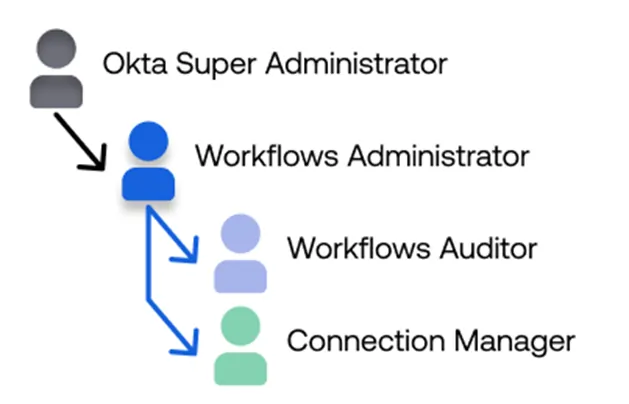
Visual 1: Okta Workflows RBAC role hierarchy and delegation path
Delegation of administrative authority in Okta Workflows without over-permissioning
Granular access control is a cornerstone of modern cybersecurity, ensuring each user has only the access needed to perform their responsibilities. RBAC enforces this principle by granting permissions through defined roles, reducing the risk of unauthorized activity.
Comparative research on access control models notes that while attribute-based approaches can offer more nuanced, context-aware permissions, they often require higher administrative overhead to configure and maintain at scale.
RBAC, by contrast, enables organizations to implement least privilege efficiently without introducing unnecessary complexity into the management process. This efficiency becomes especially valuable in environments with frequent personnel changes or large distributed teams.
The Zero Trust Maturity Model identifies RBAC as a foundational capability for limiting lateral movement within systems. In Okta, this translates into configuring roles to restrict access, such as enabling developers to test APIs only within sandbox environments while shielding production systems, or allowing finance staff to view sensitive financial records without granting modification privileges.
The result is a consistent, enforceable boundary that safeguards critical systems without obstructing legitimate workflows.
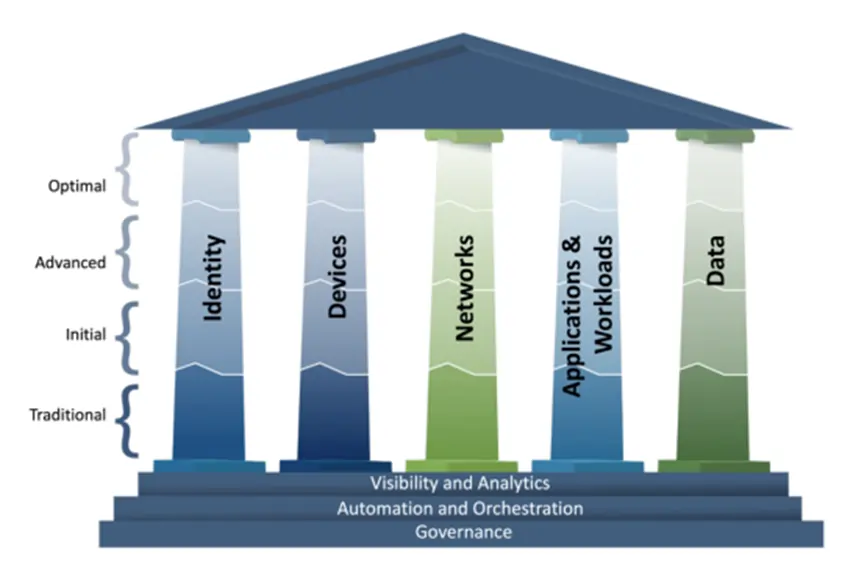
Visual 2: Access control maturity stages from CISA’s Zero Trust Maturity Model
Aligning Okta RBAC implementation with Zero Trust best practices.
Managing permissions for individual users quickly becomes unmanageable as organizations grow. RBAC in Okta eliminates this problem by assigning permissions at the role level. Once a role is configured, it can be assigned to any number of users, who then inherit its permissions automatically.
This model ensures consistency, reduces human error, and speeds up onboarding and offboarding. Okta’s Universal Directory further enhances this by allowing group-based role assignments to change in an upstream HR system, which can automatically adjust access rights without manual intervention.
The operational gains are immediate: helpdesk ticket volume drops, onboarding delays vanish, and the overall access environment becomes more predictable.

Meeting the demands of frameworks such as HIPAA, SOC 2, and ISO 27001 requires auditable, policy-driven access control. RBAC in Okta satisfies these requirements by offering an explicit mapping between job functions and access rights, making it straightforward to prove that access is appropriate and controlled.
Every role assignment and permission change in Okta is logged, providing a reliable audit trail. During compliance reviews, this enables organizations to demonstrate not only who has access to what, but also the governance process behind those assignments. According to Okta, this structured approach simplifies audits and reduces the time needed for evidence collection.
RBAC works best when access needs are stable and predictable. Attribute-Based Access Control (ABAC) makes decisions using user, resource, and environmental attributes, allowing policies to adapt to context in real time.
According to a federal study, ABAC includes components like Policy Enforcement Points and attribute repositories. In practice, many organizations use a hybrid model, called Policy-Based Access Control (PBAC), that combines RBAC’s structure with ABAC’s flexibility.
In Okta, this often means setting RBAC as the default for predictable entitlements, then adding ABAC-style rules for conditional access, for example, temporarily elevating privileges during an incident or blocking access from untrusted devices.
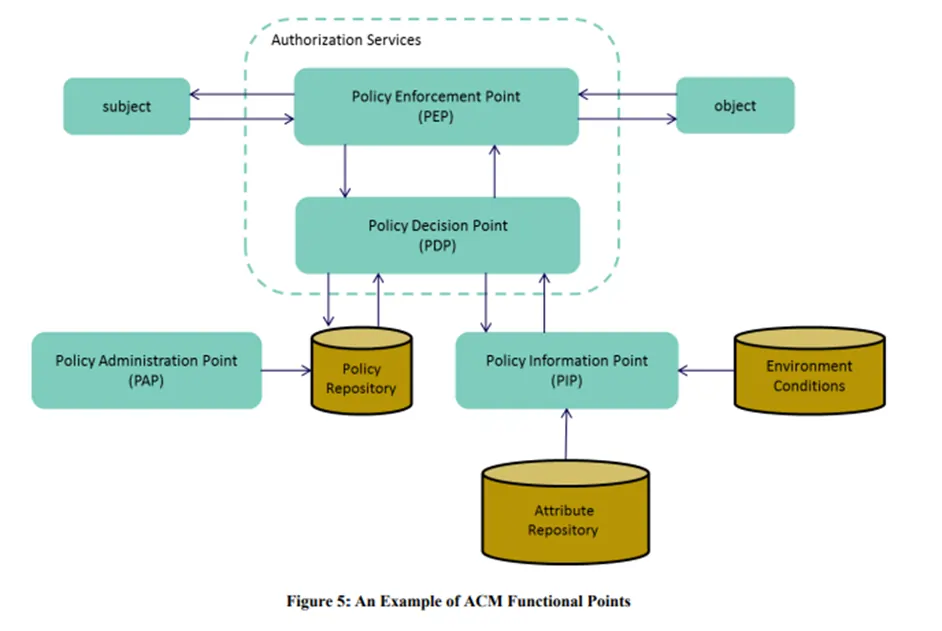
Visual 3: ABAC functional points, policy enforcement, and decision-making flow
Key components in ABAC’s decision-making model, as defined by NIST.
Drawing from Okta’s own documentation and industry practice, the following steps can guide a successful RBAC implementation:
When implemented with care, these practices prevent the common pitfall of role proliferation while maintaining flexibility for future changes. The example below shows a simple JSON role definition for a “Developer” role. It grants developers sandbox write access while restricting production to read-only.
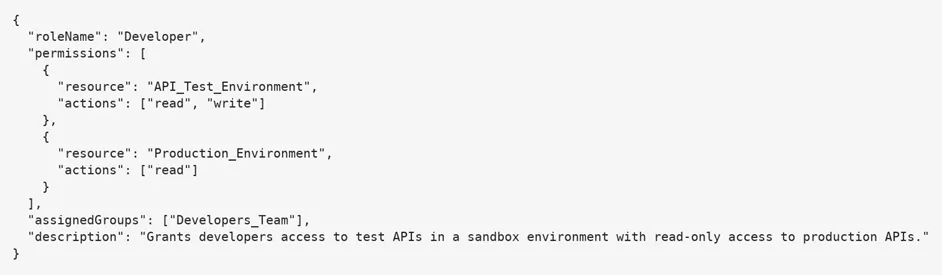

When implemented with discipline, RBAC in Okta can transform access management from a reactive task into a proactive control system. The same structure that makes it effective, however, can present challenges if it is left unmanaged. Understanding both sides of the equation is key to sustaining long-term value.
Organizations often hesitate to embrace RBAC because of perceived complexities. One concern is the risk of role conflicts, where a user may inherit excessive permissions from multiple roles. This is best addressed through routine audits and automated conflict detection.
Another challenge is scalability. In Okta, integrating RBAC with group-based provisioning and HR systems ensures that role assignments adjust automatically as teams grow or reorganize. Finally, there is the matter of keeping the RBAC model relevant over time; a structured schedule for reviewing and updating roles helps maintain alignment with evolving business needs.
Q1. How do I avoid role conflicts?
Regularly review roles, enable conflict detection, and limit each user to one primary role unless approved.
Q2. Can RBAC scale in large enterprises?
Yes, link roles to HR-managed groups in Okta’s Universal Directory for automatic updates during team changes.
Q3. What audit reports can Okta generate?
Okta logs all role changes and can export access history for compliance frameworks like HIPAA, SOC 2, and ISO 27001.
RBAC in Okta is not just a security feature, but a framework that supports the long-term scalability, compliance, and operational efficiency of an organization’s access management. By starting with clearly defined roles, applying least privilege consistently, automating where possible, and reviewing regularly, organizations can realize both immediate and enduring benefits.
The combination of Okta’s robust role management capabilities with disciplined governance practices creates a powerful platform for securing resources without impeding productivity. As access control models evolve, integrating RBAC with complementary approaches like ABAC will enable even greater adaptability in the face of shifting security and compliance landscapes.
About the Author
Prashanthi Gutha is an experienced technology leader specializing in identity and access management, security architecture, and scalable enterprise solutions. With a background spanning secure systems design, access governance, and cloud integrations, she has guided complex, mission-critical projects across global organizations. Her work blends deep technical expertise with a focus on compliance, operational efficiency, and sustainable security frameworks.







