Home Technology Software Bronze Butler Exploits Zero-Da...
Software
CIO Bulletin
31 October, 2025
Chinese hackers are using zero-day vulnerability in Japanese software LANSCOPE to attack corporate systems with complex malware.
A fresh cybersecurity alert has surfaced as cybersecurity researchers at Counter Threat Unit (CTU) discovered a complex cyberattack by the BRONZE BUTLER collective using a zero-day bug in Motex software, the LANSCOPE Endpoint Manager. The organization, which is supposedly sponsored by the state and headquartered in China, has a track record of attacking Japanese technology companies.
CVE-2025-61932 is the software vulnerability that permits remote attackers to execute the commands with the full system privileges. Even though there are not many internet-facing devices under vulnerability, hacked systems may facilitate escalation of privileges and subsequent lateral movement in corporate networks. The JPCERT/CC of Japan found the vulnerability and issued an advisory, and the U.S. CISA put the vulnerability in its Known Exploited Vulnerabilities Catalog.
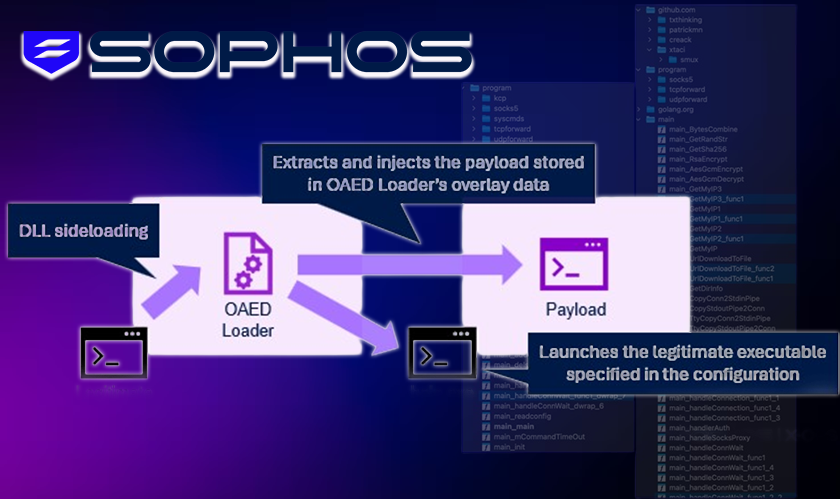
Researchers have found out that BRONZE BUTLER used the Gokcpdoor and Havoc malware families to manage the infected software environments, steal data, and evade detection. Other legitimate tools that the attackers resorted to included 7-Zip and Remote Desktop in order to cover up malicious activity.
Researchers suggest that all the vulnerable software versions should be updated now and the internet exposure of LANSCOPE servers should be limited. The mythicalized attack highlights the increasing risks to enterprise endpoint management software, particularly within the tech sector in Japan.







